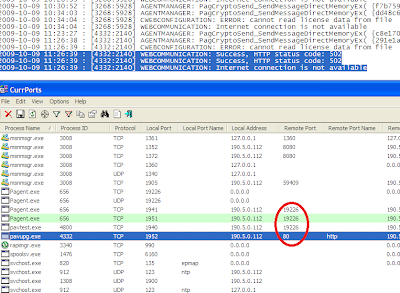
Various network administration tools take advantage of the WMI component to know how their co-workers computers are doing, or what the co-workers are doing with it. This information is passed to those tools trough the WMI Classes. So suppose you don't want to tell them what software you have installed on your computer, then, without stoping WMI service ( leading to the administrator knowing that there was a scan error with your machine ) you can instead delete the WMI CLass Win32_Product and Win32_ProductCheck, lets see:
On the command line:
c:\> wbemtest
( the wbemtest window pops up on Windows)
Click Connect, and where it says root\default replace with root\cimv2 press OK
Now press the button Enum Instances... and you should see:
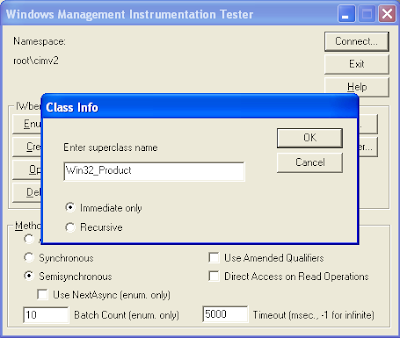
There enter Win32_Product and accept, you should see a bunch of entries like this:

You can conclude that Win32_Product class is announcing that i have, among lots of other stuff, Microsoft Office installed.
To stop this class from reporting software, the simpler solution i know is to delete the class. Just press where it says Delete Class and enter it's name, but beware: I don't think there is a practicall way to reinstall this class again unless you fully reinstall WMI. So proceed wisely.
Of course, there are other ways to obtain the installed software on your machine remotely. :)
Thanks for reading